Quick Read
- Check Point Research uncovered the YouTube Ghost Network, distributing malware via over 3,000 infected videos since 2021.
- The campaign targets users searching for cracked software and game cheats, with attackers rapidly adapting to security countermeasures.
- Disney has warned YouTube TV subscribers of a possible blackout for ABC, ESPN, FX, and other channels if a new deal is not reached by October 30.
- YouTube TV serves an estimated 10 million subscribers, making the dispute’s outcome critical for viewers.
YouTube Ghost Malware Network: A New Era in Cyber Threats
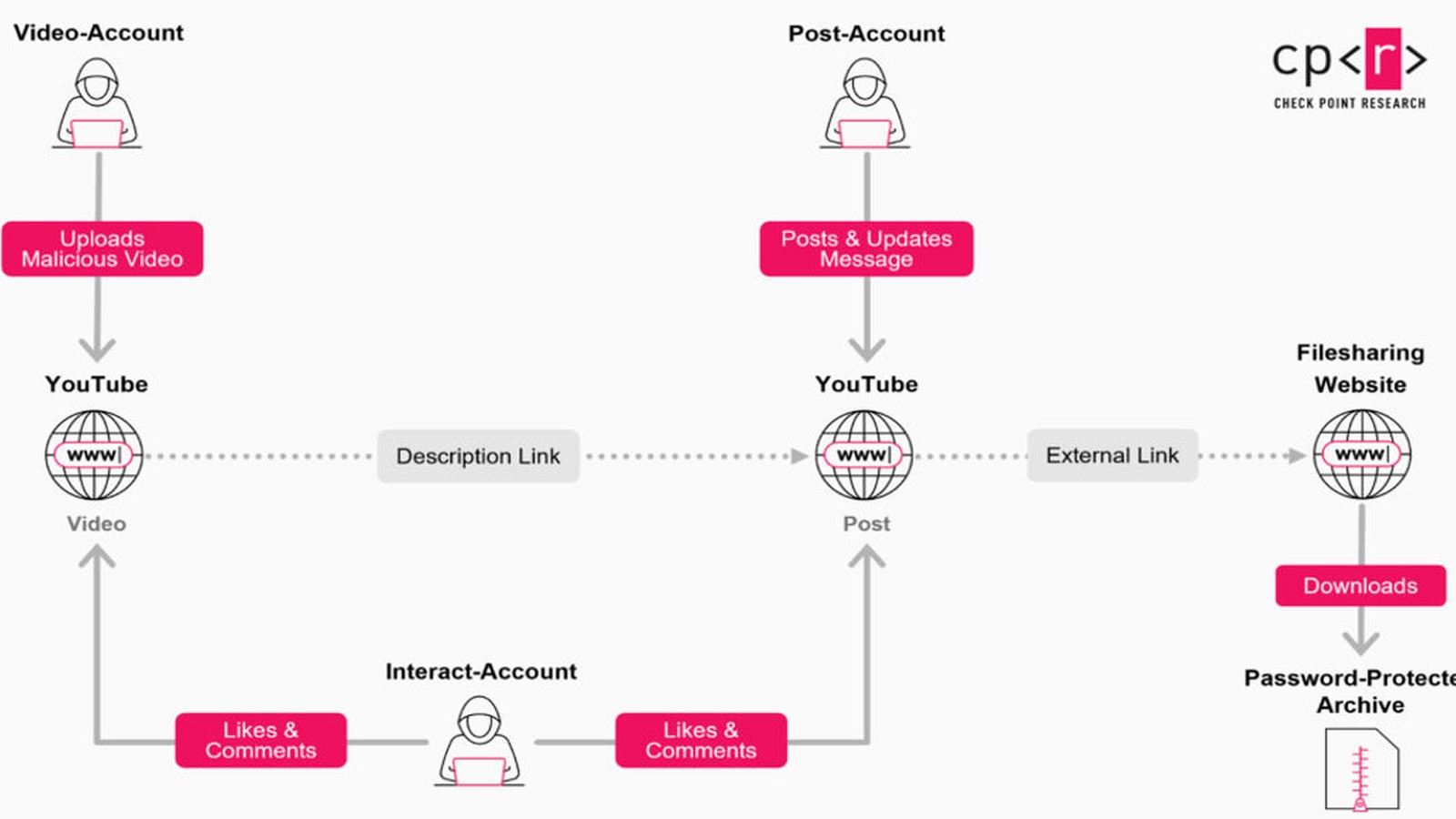
In a troubling shift for internet security, Check Point Research has exposed the ‘YouTube Ghost Network,’ a sophisticated malware operation that’s weaponizing YouTube’s global reach. This isn’t your average phishing scam. Instead, it’s a carefully orchestrated campaign involving more than 3,000 malicious videos, all designed to infect users with powerful information-stealing malware.
Since at least 2021, the Ghost Network has evolved rapidly. But 2025 marks a turning point: activity has tripled, with cybercriminals now exploiting the inherent trust users place in the YouTube platform. By moving beyond classic email phishing, attackers tap into YouTube’s legitimacy, making their schemes much harder to spot—and much more dangerous.
According to GBHackers News and CyberPress, the operation’s structure is alarmingly robust. Three distinct account types work together: video uploaders push malicious content, post publishers share download links and passwords, and interact accounts flood videos with fake likes and comments to boost credibility. This role-based system means that even when accounts are banned, replacements pop up quickly, keeping the campaign alive.
Who’s Being Targeted—and How?
The Ghost Network zeroes in on users searching for ‘Game Hacks/Cheats’ and ‘Software Cracks/Piracy’—popular but risky categories where curiosity and the promise of free tools lure thousands. The most successful malicious video, a cracked Adobe Photoshop installer, racked up nearly 293,000 views. Another targeting FL Studio reached 147,000. These numbers far exceed the reach of traditional malware emails, underlining how social platforms amplify risk.
Videos often instruct viewers to disable antivirus tools like Windows Defender, a step that leaves systems vulnerable. Download links, typically hidden in video descriptions or pinned comments, lead to password-protected archives hosted on services such as MediaFire, Dropbox, or Google Sites. These archives masquerade as legitimate software but contain infostealers like Lumma and Rhadamanthys, designed to siphon credentials and financial data to remote servers.
What’s especially insidious is the multi-layered deployment. An initial installer (often MSI) delivers HijackLoader, which then downloads the final payload. Some archives even contain functional cracked software, making victims less suspicious as the malware works silently in the background.
Malware Evolution and Evasion Tactics
Industry shakeups have influenced which malware the Ghost Network distributes. Lumma was the dominant infostealer until law enforcement cracked down in early 2025. In response, threat actors quickly pivoted to Rhadamanthys, demonstrating an unsettling adaptability. The malware’s infrastructure—command-and-control servers—rotates every few days, dodging detection and reputation-based blocking. Antivirus engines often lag behind, with new malware variants appearing before security databases can catch up.
Researchers found that compromised YouTube channels with thousands—even hundreds of thousands—of subscribers were leveraged to spread malware. One campaign hijacked @Sound_Writer, focusing on cryptocurrency scams, while another compromised @Afonesio1 to distribute infected Adobe installers to content creators. Attackers used multiple hosting platforms for redundancy, ensuring their payloads remained accessible even as individual links were taken down.
It’s a strategy that exposes a critical weakness: social engineering is now intertwined with platform trust. By exploiting YouTube’s popularity and user engagement features, criminals have built a self-sustaining ecosystem. As CyberPress notes, ‘coordinated efforts between platform operators, security vendors, and law enforcement are crucial to combating future Ghost Network operations.’
Disney and YouTube TV: A Content Blackout on the Horizon
While YouTube grapples with cyber threats, its TV service faces a different crisis. Disney has warned that, unless a new distribution deal is reached by October 30, YouTube TV subscribers could lose access to ABC, ESPN, FX, National Geographic, and the Disney Channel. Notices began airing on Disney’s cable networks and ABC stations, alerting viewers that major sports programming—including NFL, NBA, NHL, and college football—could disappear overnight.
The dispute, reported by Seeking Alpha and Broadband TV News, centers on carriage fees and contract terms. Neither company has disclosed specifics, but the stakes are high: YouTube TV boasts an estimated 10 million subscribers, each paying $82.99 monthly for access to these channels. Recent months have seen similar standoffs, including a narrowly avoided loss of Fox networks and a week-long Disney blackout on DirecTV in 2024.
Both sides insist they want a ‘fair’ deal, yet the risk of a blackout looms large. If no agreement is reached by the deadline, YouTube TV will go dark for Disney’s channels until negotiations resume. The immediate impact falls on sports fans and families, but the broader issue is about the shifting power dynamics in media distribution. With streaming platforms and content providers locked in recurring disputes, the future of TV access remains uncertain.
Platform Trust Under Pressure
The twin crises highlight a fundamental challenge for YouTube: maintaining user trust in an era of escalating threats. On one front, its open nature and mass appeal make it an attractive vector for cybercriminals, who exploit features designed to foster community. On the other, its role as a virtual cable provider exposes it to the vagaries of corporate negotiation and content licensing.
For ordinary users, the implications are clear. The promise of free software or game cheats is often a trap, while the convenience of bundled TV channels can vanish with a contract dispute. Both scenarios reveal how much we rely on platforms like YouTube—not just for entertainment, but for essential services and daily routines.
Security experts urge vigilance: avoid downloading cracked software, scrutinize video descriptions for suspicious links, and keep antivirus tools enabled. Meanwhile, viewers are left watching the clock as Disney and YouTube TV race toward a deadline that could reshape streaming access for millions.
Assessment: The convergence of massive malware campaigns and high-stakes media negotiations exposes critical vulnerabilities in YouTube’s ecosystem. While platform trust has long been its biggest asset, these events show that technological convenience and content abundance come with hidden risks—requiring not just better security and business practices, but a more informed, cautious user base.